P: 7,
Ahmia search engine phishes users.
P: 4,
How to learn R?
P: 9,

They don't exist right now it seems
P: 23,

How do I know if my USB WiFi Adapter or USB drive has DMA?
P: 92,

Nanonymity lore iceberg
P: 3,

i2p user hosted mirror for video.
P: 39,
Uniting for Internet Freedom: Tor Project & Tails Join Forces
P: 30,

Tor Only Firewall?
P: 172,
Juniority
P: 4,

P: 18,

How do I encrypt my RAM on linux?
P: 11,

unbridled autism moments
P: 8,
is C23 a waste of time?
P: 9,

>tfw no GNU/XMR
P: 69,
Forgetting LUKS password
P: 5,

tech
P: 18,

The reasons some people still use Windows, that I can think of.
P: 9,

P: 89,

Google aka Gulag
P: 4,
12of7
P: 4,

P: 31,
What computers support flashing BIOS internally?
P: 7,

Dealing with chat bots.
P: 44,
cde-desktop blog
P: 73,
invidious is dead, therefore youtube is dead to me.
P: 17,

Kermit
P: 12,

P: 27,

P: 14,

P: 128,
Tor broken through guard discovery attack (2019-2021, Published 2024)
P: 19,

Backup solutions
P: 7,

Mirrors for breachforums?
P: 1,

P: 23,

P: 31,

Some scary stuff
P: 14,
Web server thread
P: 3,

well interesting ad
P: 15,
P: 14,

P: 6,

Kristall
P: 1,
Rust declarative macro bs
P: 33,

I2pchat
P: 4,

VT100 text art
P: 63,

De-google your phone!
P: 5,
Crypto Questions Thread
P: 16,

/rust/
P: 7,

Whoopsies! USA ISPs were giving access to the C***** to all their users data, phone calls, and real time IPs.
P: 10,

anon thoughts
P: 6,

P: 3,

P: 9,

P: 35,

Laptops are gay
P: 67,

Hidden microphones and cameras
P: 53,

Entertainment media copyright madness
P: 10,

P: 15,
KYC
P: 15,
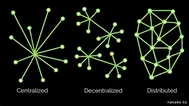
"Decentralized" as a discrete term or a relative term?
P: 14,
Learn to code!
P: 10,

P: 74,

P: 9,

Linux distro chooser
P: 9,
IT Certifications
P: 5,
12of7
P: 6,

Wireless long range communications
P: 18,
why do we waste our brains doing nothing
P: 5,
My tor connection is almost as fast as clearnet, always.
P: 19,

ungoogled-chromium / Iridium browser
P: 18,

Slackware Logo
P: 17,

NPU (Neural Processing Unit) chips
P: 5,

A bot attack on a site, service, or protocol is just a sophisticated DDOS attack to suspend functionality.
P: 23,
Exploiting Leakage in Password Managers via Injection Attacks
P: 4,

Theorists theorise
P: 2,

if you want it
P: 5,
Digital file piracy analyzed
P: 12,
P: 4,

P: 6,

love the credits theme
P: 9,

Kali
P: 19,

84% of Americans (sic) what tougher online privacy laws
P: 8,

the power of pentium i mmx
P: 11,
I use facebook for marine communication
P: 24,

Post-quantum cryptography
P: 110,
Best operating systems
P: 6,
What is the difference between classic https and http .torify.net
P: 82,
Absolute state of Privacy Guides
P: 2,

P: 17,
Is Tor slowing down?
P: 7,
could linux/unix-like systems reduce more e-wastes?
P: 2,

Do you think you need a prescient navigator like in the Dune series for interstellar travel without dying?
P: 4,
Intel introduced ME in 2008
P: 102,

How risky is it to use second hand flashdrives?
P: 31,

Hardware gapping for suspicious digital files.
P: 9,

Wargames
P: 5,

libreboot help
P: 14,
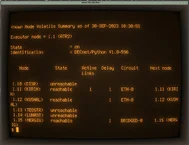
CRT
P: 15,

Working Tor2web proxies?
P: 6,

which cock in the box (VPS) for 4chin and other use
P: 14,

Looking for a good older digital camera?
P: 4,

12of7
P: 22,

0.0.0.0 Day Exploit
P: 27,

Does anyone here use Lokinet?
P: 7,
Is send-later email safe for nanonymity
P: 14,

cirrus cl-gd5446 + pentium P5 + NetBSD 10 = won!
P: 63,

the best os
P: 46,

Technology appreciation thread
P: 22,

qbittorrent 4.6.0-1 I2P Torrenting
P: 3,

MMX Technology
P: 601,

QTDDTOT
P: 4,

P: 3,

i love it
P: 8,
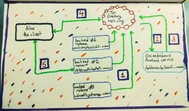
Distributed servers and other methods for more secure onion hosting
P: 9,
Database Engine
P: 34,

hacked VPS
P: 12,

unix time keep lagging behind
P: 30,

Tails OS is now a tracking app.
P: 18,

gcc segfault
P: 11,

P: 93,

Encryption doesn't work
P: 9,
8of7
P: 17,
tech
P: 14,

plan⑨
P: 4,
6to8
P: 36,

SunOS (AKA Solaris)
P: 4,
HOPE Conference thread
P: 14,

Tier B country
P: 48,

Noisy is a command-line tool for generating random DNS and HTTP/S internet traffic noise.
P: 35,

P: 13,

credentials to control python/pypi unwittingly exposed for a year
P: 30,

Why are whites like this?
P: 33,

Which is better for stability and security?
P: 9,

VM host live OS "vmdebian"
P: 16,

P: 11,

P: 20,

Tell me something cool to install?
P: 15,

99999
P: 10,

How can I obtain the dimensions of pictures from cli?
P: 5,
Is DNSCrypt good to use even if you already use Tor or I2P?
P: 58,

Computers without ME/PSP backdoor
P: 11,

P: 9,

Why is Jackie Chan CEO of Nvidia?
P: 84,

libreboot snakeoil
P: 6,

Manually upgraded Liberte Linux is better than Tails OS/Kodachi?
P: 8,

AI wouldn't be able to take your job as easily if your countries had data protection laws.
P: 11,

P: 13,
Mullvad Browser
P: 17,
Have you used stegsnow or gifshuffle M'Lady?
P: 18,
Opinion on Pidgin Internet Messenger? - 12of7
P: 67,

bet.i2p
P: 26,

Would Yagi Script Idea Scenario be Possible?
P: 38,

Lets actually do something for privacy?
P: 2,

P: 87,

Tor Project US Navy Project
P: 17,
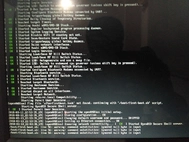
12of7
P: 224,
Uuuhhh I2P bros? What's going on?
P: 8,
12of7
P: 15,
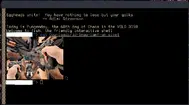
SIXEL
P: 26,

P: 3,

buying a new hardware
P: 69,

OpenBSD appreciation thread
P: 59,
Disposable VM's leave traces on your HDD/SSD even after disposal
P: 86,

Is QubesOS and TailsOS Backdoored?
P: 2,

P: 50,

IPv6
P: 1,

P: 29,
P: 29,

Fingerprinting digital files
P: 4,

Are we the ones that are wrong?
P: 72,

install gentoo
P: 79,

P: 2,
Hey! DuckDuckGo is down!
P: 125,

Whonix
P: 52,

P2P Imageboard
P: 2,

P: 31,

leaked databases
P: 3,

Mob Programming
P: 51,

beanpill
P: 14,

>Configuration-dependent
P: 6,
P: 22,

Tails OS runs SWAP by default?????!
P: 71,

What Privacy Coins are worth investing in?
P: 4,

P: 18,

Amnesiac i2P distro?
P: 2,

L(O*62).ONG
P: 72,

Tutanota is a honeypot
P: 28,

I2P torrenting on Android phones,
P: 23,

*****U
P: 2,

P: 50,

OPENWRT
P: 29,

private proxy
P: 15,

How safe is I2P really
P: 60,

profile of a un*x domain boomer
P: 23,

P: 10,

P: 19,
P: 26,

Is it a honeypot?
P: 12,

P: 14,

P: 16,

dumbass software design
P: 4,

P: 10,

How can no two PGP keys have the same fingerprint?
P: 51,
Cloudflare1.1.1.1 reverse proxy
P: 5,

P: 12,

Rust Security? 404 not found!
P: 32,

Redpill me on why should I even use these?
P: 14,

P: 10,

Thinkpad Security, Verify if Uninfected?
P: 11,
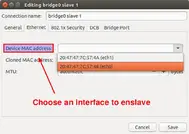
Network "CUCK" Manager
P: 8,

tailscale
P: 11,

Invidio.us clones or youtube CDN were probably distributing malware through .mp4s probably.
P: 27,

12of7
P: 10,
How do I use dd to overwrite a drive with text ?
P: 19,

Imagine the most inefficient way to do AI computing ever concieved by mankind.
P: 25,

Bashisms
P: 9,

gimp is still shit
P: 15,
Identifying computers (and users) using the emergency broadcast systems.
P: 45,

P: 57,

xz backdoored, ssh compromised
P: 6,

P: 16,

P: 11,

Imposter game used to train AI lie recognition.
P: 29,

gpg --store -a
P: 28,

P: 134,

sudon't
P: 5,
how long til wiggers r saying this
P: 60,

GNU Guile
P: 47,

P: 45,

Let's make our own modular and cheap laptops
P: 22,

P: 10,

P: 16,

I2P and floodfill
P: 11,

P: 4,

https://github.com/netsecfish/dlink
P: 9,
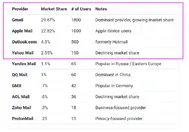
An open letter to email gate-keepers
P: 61,

Porting OpenBSD pledge() to Linux
P: 2,
Recommend clearnet and darkweb irc networks
P: 34,

Shinobi I2p Search Engine
P: 6,

Handhelds
P: 22,

P: 6,
vim
P: 23,

Why prolog is by far the best, most productive, easiest programming language
P: 71,

Linux DECNET
P: 36,

I am so pissed off at firefox.
P: 146,

Linux Distro discussion thread
P: 35,

P: 6,

quick security tip
P: 14,
how to monitor your cilents (customers)
P: 10,

Raytracing
P: 15,

P: 6,

Quandums.
P: 4,

P: 7,
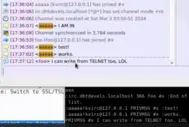
IRC on Tor: group of DHT-Devels where we discuss darknet, privacy, freedom.
P: 26,

P: 8,
This is *****ed up!
P: 36,
Programming Language
P: 33,

Does Wayland Suck??? and How to fix support Qt Applications like AppImages?
P: 12,
Why would you need this when it comes with coreutils?
P: 23,

Large language models
P: 15,

P: 179,

WHAT THE ***** I2P ??
P: 25,
Generate PGP keys in RAM
P: 7,

Best file chooser ive ever used while writing intelligent language extensions
P: 48,
w\*ggers stockholm syndrom
P: 20,
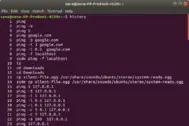
application histories
P: 24,

Hosting costs of a pastebin and bittorrent tracker website
P: 13,

P: 11,

P: 16,

P: 18,

How has nanon used ebpf in their projects
P: 6,

Why arent you using hyphanet nanon?
P: 1,
Best file chooser ive ever used while writing intelligent language extensions
P: 4,
suckless
P: 39,
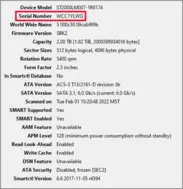
Evading device serial number tracking
P: 18,

does that shit still exist
P: 2,
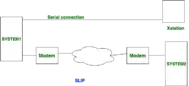
tty0tty virtual serial cables
P: 51,

P: 2,

P: 10,
Ninya's Exercise Splits
P: 6,
please verify
P: 2,
P: 18,

P: 9,

ntp/nts
P: 62,

Why do onion sites go disappearing?
P: 12,

ObeliskOne - Secure Phone
P: 19,

IMEI Changer tool on linux?
P: 4,

consider
P: 44,

P: 15,

P: 34,

Anti-stylometry and anti-fingerprinting
P: 23,

P: 3,
you cant both be right
P: 7,

Modern Secure Epistolary Writing Substrate Transfer Through Public Intermediary Deliverance Systems
P: 31,
Glowies listen to everything you do
P: 10,

P: 20,

tech
P: 74,

P: 22,
stop using webp
P: 3,

great mistakes caused by garbage tech
P: 17,
history guy RCE
P: 15,

tech
P: 27,

P: 47,

CVE-2023-4809: FreeBSD pf bypass when using IPv6
P: 29,

What happened to Tox?
P: 4,

P: 6,

P: 21,

Poast what wiby takes you to
P: 6,

Legitimate benefits of running opendrawin on not apple commodity hardware
P: 43,

Honeypot Thread
P: 12,

P: 14,

Missile intercepted in space by Israel in the first instance of space warfare in history
P: 23,

P: 2,
P: 30,

Intel Management Engine Backdoor
P: 35,
P: 5,

P: 16,

P: 12,

Gentoo goes Binary!
P: 19,
SantaRAR
P: 6,
TorZillaPrint: Firefox & Tor Browser fingerprint testing
P: 4,

P: 6,
P: 21,

BitChute is a honeypot
P: 5,

P: 7,

P: 9,

GTA 5 Source Code
P: 16,

P: 12,
Also...
P: 14,

P: 15,

Post research and sources of these Traitors!
P: 11,

P: 10,
LibrePGP
P: 20,

P: 115,

l0icense thread
P: 15,
When is GUI valid?
P: 5,

securing nginx
P: 15,

I'm thinking about writing a new kind of OpSec primer
P: 9,

P: 2,

olde-gentoo
P: 8,

Video hosting sites similar to youtube. No javascript required.
P: 12,

RF
P: 9,

P: 9,

P: 1,

P: 45,

Suggestion for linux terminal.
P: 5,

Storing secret keys offsite
P: 18,
is i2p dead?
P: 17,

Have any anons used this Hysteria?
P: 16,
P: 18,

TORDEX